Online accounts are at the center of our lives. We often access critical data, such as banking, social media, and emails, with just a single password. But is that one password really secure enough? Unfortunately, the answer is no.
Millions of accounts are at risk due to data breaches, phishing attacks, and weak passwords. This is where a simple yet highly effective method to boost digital security comes into play: Two-Factor Authentication (2FA).
In this article, we will explore what 2FA is and why it has become essential for your digital life.
What Exactly is Two-Factor Authentication (2FA)?
2FA is a security layer that requires two different verification factors to prove your identity when logging into an account. It doesn’t just ask for your password (something you know), but also requires you to verify a second factor that you possess (like your phone).
Think of it like having two locks on your front door. Your password is the first lock, but with 2FA, a second lock is added. Even if a thief steals your password, they cannot get in without the second factor (your special key).
Authentication factors are divided into three categories:
- Something You Know: Password, PIN.
- Something You Have: Smartphone, physical security key.
- Something You Are (Biometrics): Fingerprint, facial recognition.
2FA works by combining two of these different categories.
Why is a Password Alone Not Enough?
Passwords alone are weak against modern threats:
- Data Breaches: If websites are hacked, your password can be stolen. Attackers may then try it on your other accounts.
- Phishing: You could be tricked into giving your password to attackers via fake emails.
- Weak Passwords: Simple passwords like "123456" are easy to guess.
2FA acts as a shield in these scenarios. Even if an attacker knows your password, they cannot access your account without the second factor, usually your phone.
The Most Common 2FA Methods
1. SMS Verification (Text Message Codes)
The most well-known method. When logging in, a one-time password (OTP) is sent to your phone via SMS.
- Advantage: Easy to set up; no additional app required.
- Disadvantage: The least secure 2FA method. Vulnerable to "SIM swapping" attacks.
2. Authenticator Apps (TOTP)
Apps like Google Authenticator or Authy are used. They generate time-based one-time passwords (TOTP) that change every 30-60 seconds.
- Advantage: Much more secure than SMS. Works offline and isn’t tied to your SIM card.
- Disadvantage: If you lose your phone and don’t have backup codes, you may lose access.
3. Physical Security Keys (Hardware Keys)
Small USB or NFC devices like YubiKey. After entering your password, you plug in the device and press a button.
- Advantage: The most secure 2FA method. Almost completely protects against phishing attacks.
Disadvantage: Has an additional cost and must be carried physically.
4. Push Notifications
After entering your password, a notification appears on your phone asking, "Are you trying to sign in?" You tap "Approve" or "Deny."
- Advantage: Fast and easy; no need to enter codes manually.
- Disadvantage: Carelessness can lead to approving an attacker’s login attempt (“MFA fatigue”).
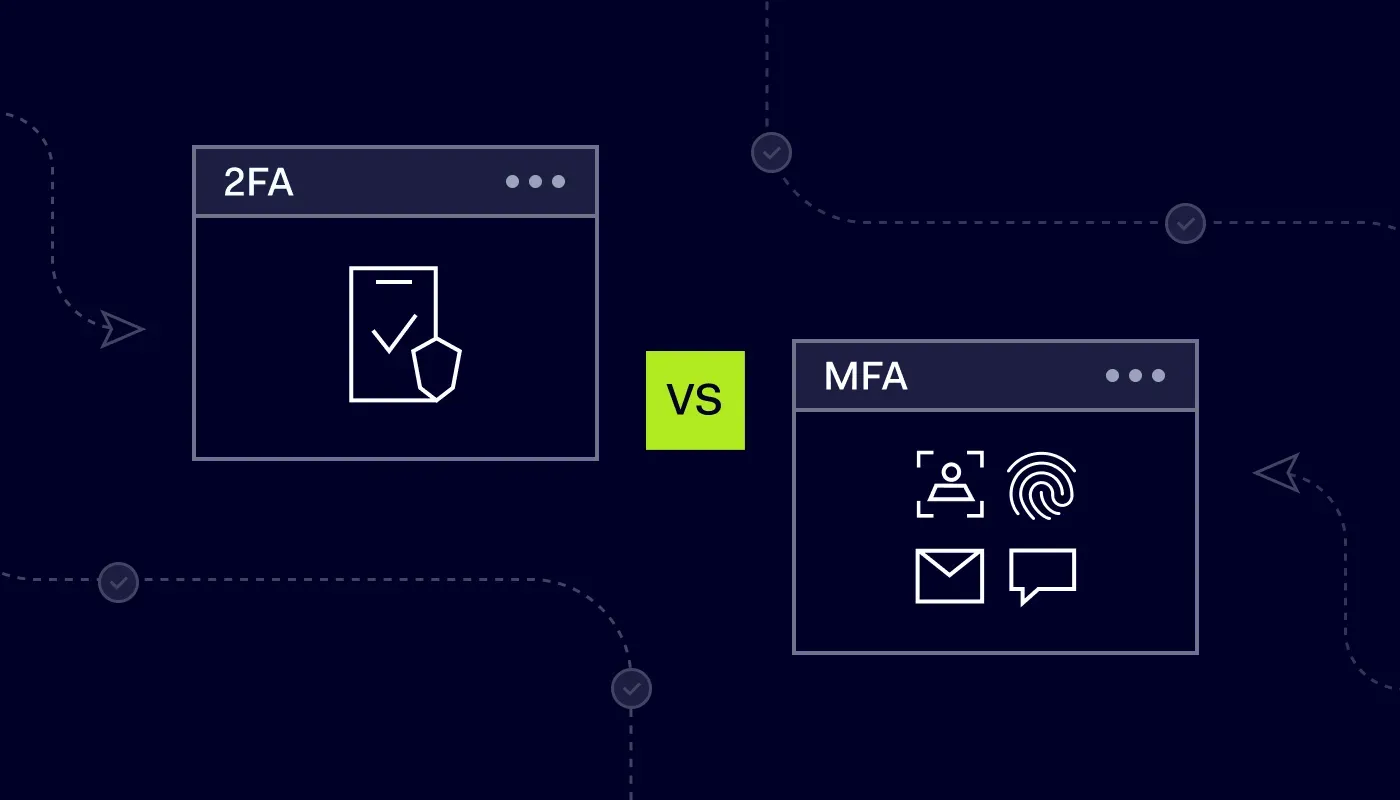
What’s the Difference Between 2FA and MFA?
These two terms are often confused, but the difference is simple:
- 2FA (Two-Factor Authentication): Requires exactly two factors.
- MFA (Multi-Factor Authentication): Requires two or more factors (e.g., password + fingerprint + security key).
In short, every 2FA is an MFA, but not every MFA is 2FA.
Time to Take Action: Boost Your Security Now
Two-Factor Authentication is no longer a luxury; it is a necessity for digital security. Setting it up takes just a few minutes but can protect you from major risks.
After reading this, go to the security settings of your most critical accounts (email, social media, banking) and enable 2FA. Whenever possible, choose a more secure option than SMS, such as an Authenticator App.
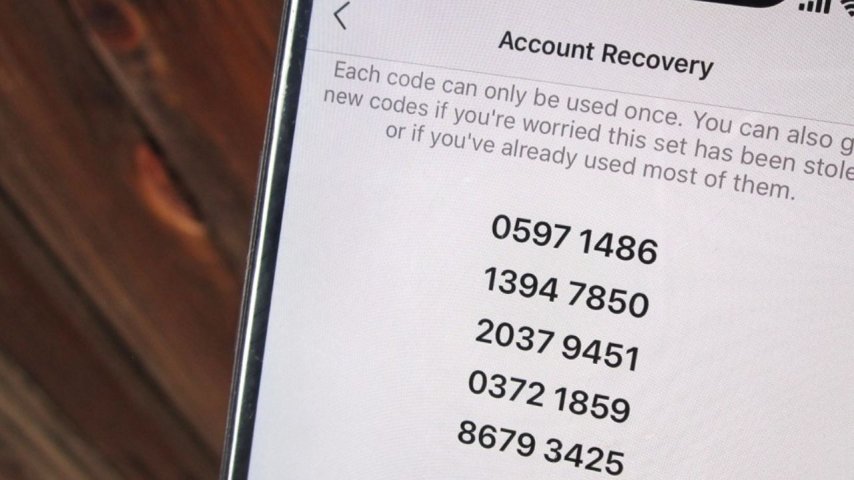
Don’t Forget Your Recovery Codes
When setting up 2FA, make sure to save the backup recovery codes in a safe place. If you lose your phone, these codes are the only way to regain access to your accounts. You can store them in a password manager or print them and keep them in a secure location, like a safe. Digital security is in your hands, and this simple step can make a huge difference.